Gmail’s Two Factor Authentication
Filed under: Security
Google recently implemented a new “two factor” authentication option for their gmail application. Two Factor authentication adds another layer of security by requiring an additional verification after you enter your valid username and password combination. This makes it more difficult for a malicious user that may have stolen your password to actually access your account. Google’s implementation reminds me of the RSA token’s work when accessing a corporate VPN or some other websites that support them. After you enter your user name and password you get a request for this additional “token.” The token is generated in one of two ways:
* Small subset of Pre-Printed codes that work only once.
* The token is created on a mobile application on your phone. (These tokens change every minute or so.)
I have a few gmail based email accounts so I thought I would see how easy it is to set this up. The first obstacle I ran into was that my gmail accounts are linked through Google Apps. When I logged into my account I was not able to find a way to enable the two factor authentication. After a bit of searching I found out that I needed to “Manage this Domain” to allow my users to even use this feature (see screen shot below).
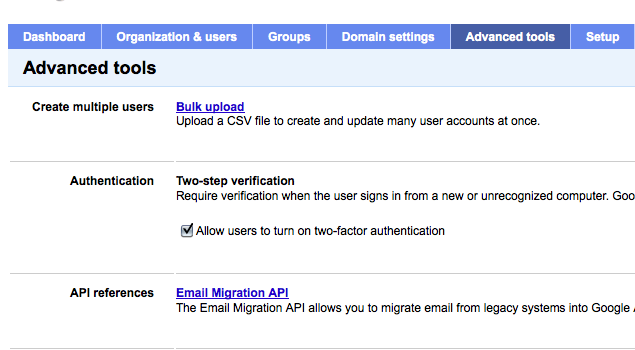
Once I enabled this feature, I was able to enable it for my individual email account. Google did a great job of creating a wizard to walk you through the process. The first step is selecting your phone type. I have an IPhone so it gave me instructions on how to download the google authentication application from the app store.
Once I got the app up and running on my phone, the web page displayed a bar code for me to scan with it. Once it scanned the bar code it automatically recognized my email account. It asked me to verify the number on the iphone app on the web page. Once it was verified I was given a list of 10 hard-coded keys incase I didn’t have my phone available. They also give you the option to set up another phone as a backup.
You might be wondering what happens if you are using Outlook, Entourage, your phone, etc, to access our gmail. These obviously don’t support the 2nd form of authentication. Google is way ahead of you. They created application “keys” that you can create for each application you want to access your account. You generate the key on the website, then use that as the password on your mail client. I was able to set all of this up (3 different clients) within about 10 minutes.
Google makes a very great effort to warn you about the new authentication and does everything they can to make sure you are set up properly so you don’t lose access to your mail.
Don’t want to have to enter a code every time you access gmail? You are in luck. You can specify that you want it to remember that specific computer for 30 days if you would like. This makes it convenient and the risk is small unless someone has stolen your password and has access to your computer.
If you are using Gmail, I highly recommend taking the time to set this up. It is a pretty cool feature and hopefully we will be seeing banks and other sites taking some strides toward this.
I don’t doubt that we will see the security guys start hammering this new feature to attempt to show any weaknesses. Even if they find some, this is still a good thing. Either way, it will not decrease your security and if anything is found, it will only help make the feature better.
Call for Education or Need for Better Applications?
Filed under: Security
The fallout from the recent VA issue http://www.nextgov.com/nextgov/ng_20101222_6852.php has made me think about one issue around software security. Is it a lack of security education or out-dated applications that lead to some of these breaches. In this example, the users apparently wanted to be able to share their calendar among multiple employees. I am sure there are many people that have had this same request. There are many solutions to this, but which one is right depends on your environment.
Education
Many users are not aware of all the compliance requirements that exist. With HIPPA, SOX and others, it can be difficult to keep up with it if you are not a security professional. Even some of the information protection standards that corporations may have can be difficult to interpret. Maybe more education on what type of data needs to be protected might have been successful.
How many users do you know that don’t have a strong understanding of the internet or what the “cloud” even is? We, as IT professionals are expected to understand this much more in-depth than those not in this industry. Just as those in the health care industry are expected to understand health more than us. Users may not understand how these technologies work, or how they may be susceptible. When a typical user thinks about sharing a password with a co-worker they do not share the IT concerns. IT is concerned with audit trails, non-repudiation, etc.. Is it possible for the general user community to have the understanding to really make legitimate decisions when it comes to using third party apps with internal data? The IT department must be involved to offer the experience, but that too can be difficult when the company is small or the IT department is limited.
Better Applications
Are many of the applications we use out-dated? Of course they are. Technology is moving fast, where most applications are updated more than once a year. There are new applications coming out every day to solve the problems of older applications. Workers want to do as little as possible, this is not a fault, but the way of life. Why work harder when we can work smarter? When a user sees a new application that solves their problem, and it is probably free, they want to jump on it. Why use an excel spreadsheet to track scheduling when you can use a nifty online application accessible by everyone from anywhere? The intent is not to cause a “breach” as stated in this case, but to make the user’s life easier. This was not malicious. It was a case of something better coming along, and how often is that happening these days?
Unfortunately, this problem is not easily solved. Many IT departments are small, with very limited resources to create new applications. Even if they did, they may be out-dated by the time they are completed. It is also difficult to even have staff to research or understand the offerings already available by third parties. How does a company, with limited IT resources, manage their data and control access to this type of “breach”? Until there is an answer to that question, I believe there will be many more of these findings.
Hopefully, as time goes on, users will become more knowledgeable about how these technologies work and how the data they work with needs to be protected. As IT professionals, we need to do a better job of assisting users with protecting their data. It is obvious that every application cannot list out all the uses, but there has to be a way some assistance can be provided.
Enhancing the UI with Greasemonkey
Filed under: Development
Have you ever used a web application and wished that it would act a little differently to make your day easier? I recently ran into this with an external application. There were sever sets of data (tables and list boxes) that would be much more useful if they were sortable. Unfortunately, since I am not the developer of the application, I am not able to directly change the application to suite my particular use cases.
I turned to Greasemonkey, a FireFox add-in, to solve my problem. Greasemonkey provides a way to add your own custom javascript to any given web page that you are visiting. In my case, there were two pages in particular. The first page, I wanted to sort one of the list boxes alphabetically. The second page, I wanted to make a data grid sortable by multiple columns. This is often necessary when working with large sets of data to get useful data.
For the first page, I wrote a script that would add a sort button, and some javascript to the page to sort the list box. Greasemonkey recognizes that the script goes with the specific page and automatically runs the javascript file I created on page load. Now, when I visit the page I see a “Sort” button. When I click it, it sorts the list box for me. This small change cuts minutes off of each time I use this particular functionality because the listbox is pretty large.
For the second page, I wanted to make a large data table sortable by clicking the headers of specific columns. This was a bigger headache, because the code samples to sort an HTML table are all for Internet Explorer. I found that Internet Explorer adds some table functions that FireFox doesn’t support. This caused a lot of troubleshooting. In the end, I had clickable column headers that would sort the table by that column. This enhancement does help reduce time, but it also helps analyze the data. With the ability to sort the data by specific columns I can easily interpret the data instead of trying to search the entire table for specific data.
I understand that development teams are under constant pressure to add functionality to their applications. I also know that the features that are added are based on the mass, not on a few individuals. It is nice to know that, with a little javascript and time, you can make these types of changes to an application. I am sure there are more ways to use Greasemonkey and encourage you to take a look at this great tool. You may be surprised at what type of scripts are already created.
SDL Regex Fuzzer
Filed under: Development, Security
Updated 11/2/2010
Microsoft has released a new “Free” tool called the SDL Regex Fuzzer. You can download the tool from Microsoft’s Download Center here: http://www.microsoft.com/downloads/en/details.aspx?FamilyID=8737519c-52d3-4291-9034-caa71855451f. The Regex Fuzzer is used to test regular expressions to see if they are vulnerable to Denial of Service Attacks (ReDoS). A Regular expression denial of service attack uses a specially crafted value for the regex to parse that ends up using a large amount of resources. This could be particularly dangerous in a cloud situation where the users pay for the CPU usage and other resources. Running those resources up could run the bill up as well. This tool can be added to the SDL process to verify regular expressions before they get into production.
Update:
More information about ReDoS can be found here: http://www.owasp.org/index.php/Regular_expression_Denial_of_Service_-_ReDoS
When I first ran the application, I received a MethodNotFound exception in System.Threading. Installing .Net 3.5 SP1 resolved this issue.
Firesheep: A Repudiation Issue
Filed under: Security
I recently posted on some of the hype surrounding the new Firesheep FireFox extension. Today, ComputerWorld (http://www.computerworld.com/s/article/9194159/Is_it_legal_to_use_Firesheep_at_Starbucks_) had an article discussing the legal issues around the use of the tool. I believe the legal aspect is important, but could be very difficult to prove. I am more interested in the implications that this tool can have of the authenticity of the information found on some of the social sites.
We have all heard stories about employers checking Facebook or MySpace regarding their current or future employees. Some people have been fired or not hired based on content on their social sites. Relationships have been dissolved because of the information found on a spouse’s network. Most recently, cyber bullying has become a huge problem among school age users.
I will use Facebook as the example because it is one of the most known and understood social networks. If there is a tool that exists that makes it fairly simple for others to post to your wall (Firesheep), then to what extent can the information on your wall be trusted? Does this new tool make it easier for the offender to say that they did not post that message and that it must have happened while on a public hotspot? If the message was actually posted while at a public place, is it possible to prove whether or not the actual user posted it or not? I guess you could review the logs to look at the user-agent and look for anomalies, but a savvy user could defeat that very easily. It would be pretty difficult to show which computer actually did the post.
What does this effect? Remember that employee that got fired for posting something offensive or against corporate policy? Did he post it? Did an attacker post it? We run into an issue of repudiation. If they cannot prove the user did or did not post the material then you cannot find them guilty. This could make it difficult for employers, or other entities from relying on information on these sites.
I understand the point of the tool is to show the weaknesses in the security for these sites. I believe that it should also show that the information found on these sites may not necessarily be as accurate as we once thought. Use the information with caution, as it could come back to haunt either party.
Firesheep: What’s the hype?
Filed under: Security
Recently, a new FireFox extension was released called FireSheep. If you haven’t heard about it yet, I am sure you will soon. If you are interested in it, a quick google search will pull up many details. There has been a lot of blogs and other articles written about this new tool, some good, some very inaccurate. So what is all the talk about this tool? Is it as bad as it appears?
What does it do?
Firesheep takes the work out of session hijacking of many popular social networking type sites (see Session Hijacking Below). When a user logs into Facebook or many other sites, they log in via a secure connection (https:). This is, of course, to protect your password from being sent in clear text across the network for an attacker to grab. Once you are logged in successfully, many sites will switch the user back over to an un-secure connection (http:). The idea here is to increase performance because there is no need to deal with the security (encryption).
Firesheep puts an easy to use interface onto a packet sniffer designed to look for specific traffic. This traffic is not Passwords, it is cookies. The tool looks for the session cookies, once the site drops back down to an un-secure channel. Once it finds the cookie it accesses the active session and pulls down an image (if available) and the user’s name from the site the cookie is for. These items are then displayed in a side bar for the user. When the user double-clicks an account, it navigates to that site as that user taking over their session.
It is important to note that this tool takes advantage of a websites inability to secure all of its traffic. If these sites implemented SSL on all pages, this would not even work.
What is the hype?
The hype is that the tool allows my mother to do something that she would normally have no idea how to accomplish. Users can session hijack with no knowledge of how that concept even works. The impact of this really depends on the site being hijacked. Some sites, like Amazon, may let you cross between secure and non-secure sessions, but to do any administrative functions for your account, you need a secure session id. This id is not available during the non-secure communications. Other sites might make you re-authenticate before doing things like changing your password, but might let you post items or send/read emails. The tool targets very well known, widely used sites. Sites like Google, Amazon, bit.ly, and Facebook are used by millions of users every day. As mentioned, some of these have a greater impact than others. Does this mean stop using the sites? No, although we need to push these operators to take security seriously and implement safeguards to protect our information.
Where does this work?
The most obvious place for this to work is in a location with public wi-fi available. When you connect to a public wi-fi hotspot, all the traffic you send can be sniffed by all other computers on that same hotspot. Depending on the type of hardware being used, this could also be done on wired connections as well, possibly at home or in the office.
What can I do to protect myself?
Be careful about what you are viewing when on public networks. Some experts have said to use a VPN service so all of your traffic is encrypted. There are a few choices available that are less than $10 a month. There are also other Firefox extensions that can force a secure connection on these sites. The problem with these extensions is that it may be possible that the site doesn’t support secure connections everywhere and it may not act properly. At the moment, I am not aware of any Internet Explorer extensions that can help protect against this.
Session Hijacking
The Web is stateless, meaning that every time you click a link or visit a different page on the website, the server doesn’t have any knowledge of previous visits. To get around this barrier, web developers use cookies to maintain state between page visits. One, or more, of these cookies will contain a unique session id that identifies your authenticated session. This is exactly why you don’t have to enter your password for every page you visit, or why your shopping cart items are still there between visits. These session ids are like a temporary password. If someone were to get their hands on your session id, during an active session, they could use it to access your session.
Cyber Patriot III
I recently volunteered to help mentor the local Civil Air Patrol cadets in the Cyber Patriot III event. The goal of the event is to get the cadets interested in cyber defense by having them secure different systems. This scenario is defensive only. The cadets receive a virtual image that contains a vulnerable operating system (Windows or Linux based). The cadets are then given a specified amount of time to secure the system. Securing the system includes auditing/removing services, user accounts, file/folder shares, malware, and installing patches.
The teams (around 600 of them) were given two practice rounds to make sure they can connect to the scoring server and practice locking down a system. The first challenge round was on October 23, 2010. Things started off a little rough because it was the first time the cadets had worked with Windows 2003 instead of Windows XP. As a Mentor, like the coach, we are not permitted to assist during the challenges. Although the team did not make all the right decisions, they were able to learn from their errors and make really good progress before the challenge completed. Due to some technical difficulties, we were not able to see our score, so hopefully it will be available soon. Until then, we are going to continue working with the team to help prepare them for the next challenge round.
I encourage anyone with security expertise to help get involved in this great organization. for more information you can find it at http://www.uscyberpatriot.org.
Adobe RoboHelp XSS
Adobe announce yesterday that they have made available 2 updates for the Adobe RoboHelp product. There were multiple cross site scripting (XSS) and content spoofing vulnerabilities that were patched. Adobe has details about the update and the patch available at: http://www.adobe.com/support/security/bulletins/apsb10-23.html. It is recommended to update your RoboHelp installations and re-deploy the help files to help protect these applications.
SQL Injection: Common Mistake
Filed under: Security
One of the most common suggestions for remediating SQL Injection vulnerabilities is to use stored procedures. Using stored procedures can help decrease the risk of SQL Injection, but if implemented incorrectly, it can create a false sense of security. For example, look at the created stored procedure below:
CREATE PROCEDURE dbo.usp_IsValidUser ( @UserName varchar(50), @Password varchar(50) ) AS SET NOCOUNT ON SELECT MemberId FROM Member WHERE UserName = @UserName AND Password = @Password RETURN
This looks like a pretty secure stored procedure. It does not use any dynamic SQL, or the dreaded EXEC command. It is still recommended that you validate your inputs, but the parameters should not execute as SQL code, but instead just as strings.
Lets take a look at the wrong way to call a stored procedure below:
_command.CommandType = CommandType.Text; _command.CommandText = "EXEC usp_IsValidUser '" + UserName + "', '" + Password + "'";
In this example, although calling a stored procedure, is still vulnerable to SQL Injection (if proper input validation is not performed). The stored procedure may be safe, but the developer has just created an inline query to call the stored procedure. A malicious user could append SQL queries to the end of this query to run their own queries.
For example, if the user passes in a Password value that contains the single quote (‘), then they can dump out of the password parameter and append on their own queries. It is beyond this post to show detailed examples of exploiting this type of statement.
It is important for developers to keep this scenario in mind when developing and doing peer code reviews. Any time the code is appending data to send to the data store you should investigate further. Always validate the input received from un-trusted sources. Use Parameterized queries instead of string building to create database queries.
Frame Busting
An often overlooked security feature for a web application is to not allow the application (especially the login screen) to be embedded in a frame. This is often referred to “frame bustingâ€. In some browsers, it is possible to capture the keystrokes in one frame, from the parent window. This would be a problem with an embedded login form where the malicious attacker embeds a login screen in a different domain and tricks a user to attempting to login. The attacker could then capture the user name and password for that user to log in at a later time.
Pages that can be captured in any frame set may also be susceptible to click jacking. Click jacking is beyond the scope of this post, but more information can be found at http://www.owasp.org/index.php/Clickjacking.
There are a few possibilities to a layered approach to protecting against both of these attacks. Internet Explorer 8 supports the X-FRAME-OPTIONS response header. Unfortunately, this is not supported by all browsers. Mozilla is working on their own directives to do the same thing, with a more robust approach. Both of these approaches are limited because they are targeted at specific browsers.
Another approach is to add JavaScript to the pages that checks the content against the parent location. If they are not the same, it breaks out of the frame and loads the content in the main window. There is a great document discussing research about this topic at Http://seclab.Stanford.edu/websec/framebusting/framebust.pdf.
It is important for application developers to assess their designs to make sure frame busting and click jacking are addressed.



